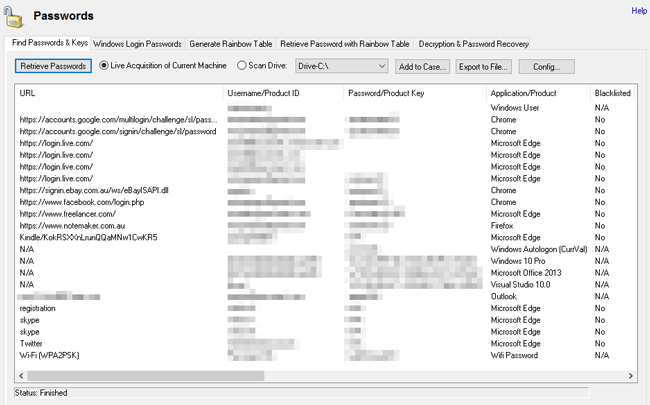
Web browser user names and passwords
With OSForensics you can recover browser passwords from Chrome, Edge, IE, Firefox, and Opera. This can be done on the live machine or from an image of a harddrive. Data recovered includes, the URL of the website (usually HTTPS), the login username, the site's password, the browser used to access the site & the Window's user name. Blacklisted URLs are also reported, showing the user has visited the site but elected not to store a password in the browser.
OSForensics also recovers the following:
- Outlook and Windows Live Mail passwords
- Saved Wifi passwords
- Windows autologon password
- Windows 7, 8, and 10 product keys
- Microsoft Office & Visual Studio product keys
- Ports (Serial/Parallel)
- Network adapters
- Physical and Optical Drives
- Bitlocker detection
Rainbow tables & hash cracking
Rainbow tables are large tables of plain text passwords and hashes. They allow a password to be quickly looked up if a hash for that password is known.
OSForensics can both generate and use rainbow tables for the MD5, LM, NTLM and SHA1 hashes. Free example rainbow tables are available on the download page.
Decryption & password recovery of office documents
OSForensics supports two methods of gaining access to encrypted office documents.
The first method is for older documents that use 40bit encryption (old XLS, DOC & PDF files). For these documents is it possible to try all possible keys to decrypt the document, with the output being an unencrypted file.
[Coming soon] The second method is a brute force attack on documents with more up to date encryption. In this scenario it is possible to select a dictionary for a dictionary attack.




