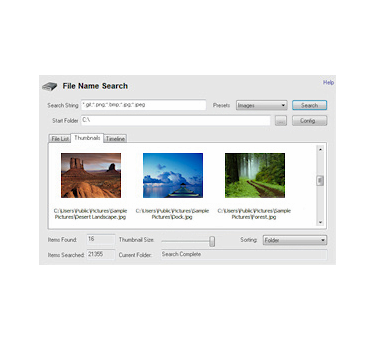
Find files quickly
OSForensics™ allows you to search for files many times faster than the search functionality in Windows.
Results can be analyzed in the form of a file listing, a Thumbnail View, or a Timeline View which allows you to determine where significant file change activity has occurred.
More »
Search within Files
If the basic file search functionality is not enough, OSForensics can also create an index of the files on a hard disk. This allows for lightning fast searches for text contained inside the documents. Powered by the technology behind Wrensoft's acclaimed Zoom Search Engine.
More »
Search for Emails
An additional feature of being able to search within files is the ability to search email archives. The indexing process can open and read most popular email file formats (including pst) and identify the individual messages.
This allows for a fast text content search of any emails found on a system.
More »
Recover Deleted Files
After a file has been deleted, even once removed from the recycling bin, it often still exists until another new file takes its place on the hard drive. OSForensics can track down this ghost file data and attempt to restore it back to useable state on the hard drive.
More »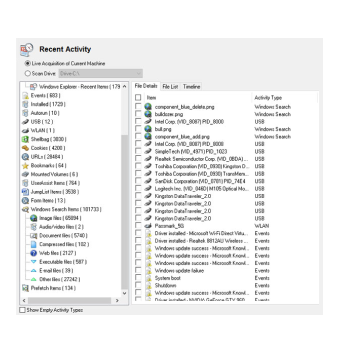
Uncover User Activity
Find out what users have been up to. OSForensics can uncover the user actions performed recently on the system, including but not limited to:
- Opened Documents
- Web Browsing History
- Connected USB Devices
- Connected Network Shares
Find out more about uncovering user activity here »

Collect System Information
Find out what's inside the computer. Detailed information about the hardware a system is running on:
- CPU type and number of CPUs
- Amount and type of RAM
- Installed Hard Drives
- Connected USB devices
and much more. Powered by Passmark's SysInfo DLL. More »

View Active Memory
Look directly at what is currently in the systems main memory. View 47 columns of metadata for each process. Attempt to uncover passwords and other sensitive information that would otherwise be inaccessible.
Select from a list of active processes on the system to inspect. Capture process specific binary dumps for later viewing.

Extract Logins and Passwords
Recover usernames and passwords from recently accessedwebsites in common web browsers, including Internet Explorer, Firefox, Chrome and Opera.
More »
Detect Hidden Disk Areas
Discover hidden disk areas (HPA/DCO) of a hard disk. Attempt to expose sensitive information that would otherwise be inaccessible.
Remove or create an image of the hidden areas for further analysis.
More »



