How to examine Mac and Linux hard drives with OSForensics?
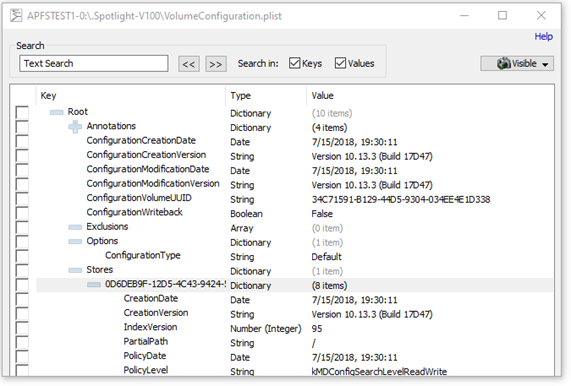
OSForensics has support for direct image access of Mac (APFS/HFS+/HFSX) and Linux images (Ext2/Ext3/Ext4), so it is possible to view and investigate Mac and Linux file systems using OSForensics on a Windows system. Many of the major OSF modules can be utilized with a Mac of Linux image file. You can parse the file system with the File Name Search module, run the Recent Activity scan to uncover user activity, data carve the image to recover deleted files, and extract browser passwords and user account information in the Passwords module. Other modules such as Create/Search Index, the Raw Disk Viewer and others can also be utilized on most Mac and Linux systems. You can also manually drill down into the file system by using the File System Browser module. Starting in version 6, Apple's latest APFS file system is now supported; including support for compression (zlib & lzvn) and encryption. We also have a built-in PLIST Viewer located on the Start screen, which will allow you to view Apple's PLIST files and add them to your case.
While generally there is no need, if you did need to mount the image with a drive letter this requires a 3rd party file system driver to be installed such as the following:
- Paragon APFS for Windows (Mac APFS file system)
- Paragon HFS+ for Windows (Mac OS HFS+ file system)
- Ext2Fsd (Linux ext2/ext3/ext4 file systems)
The following table summarizes the OSForensics functionality that is available for Linux/Mac drives
Feature Windows file systems Mac/Linux file systems File name searching Disk indexing and searching All file types except unallocated sectors Detect recent activity (Windows & Mac) Deleted files searching (data carving) Mismatched files searching Raw disk viewer Find passwords Verify & create hash Create and compare signatures
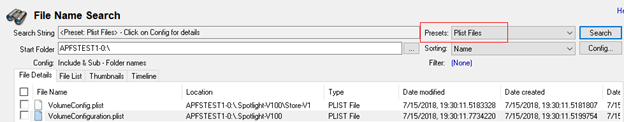
PLIST File Search on an APFS Image File in the OSF File Name Search module:
PLIST Viewer: