How to view hidden NTFS files
You can view hidden NTFS files on a disk image or hard drive by using the file system browser in OSForensics. In the file system browser choose "Add device to case" from the File menu and select the drive letter or image file you wish to view. Pick 'Forensics mode' when adding local hard drive as a device.
The example below compares the file listing, in Windows Explorer, from an image file that has been mounted to a drive letter to the file listing in the file system browser after directly opening the image file, note the files beggining with "$".
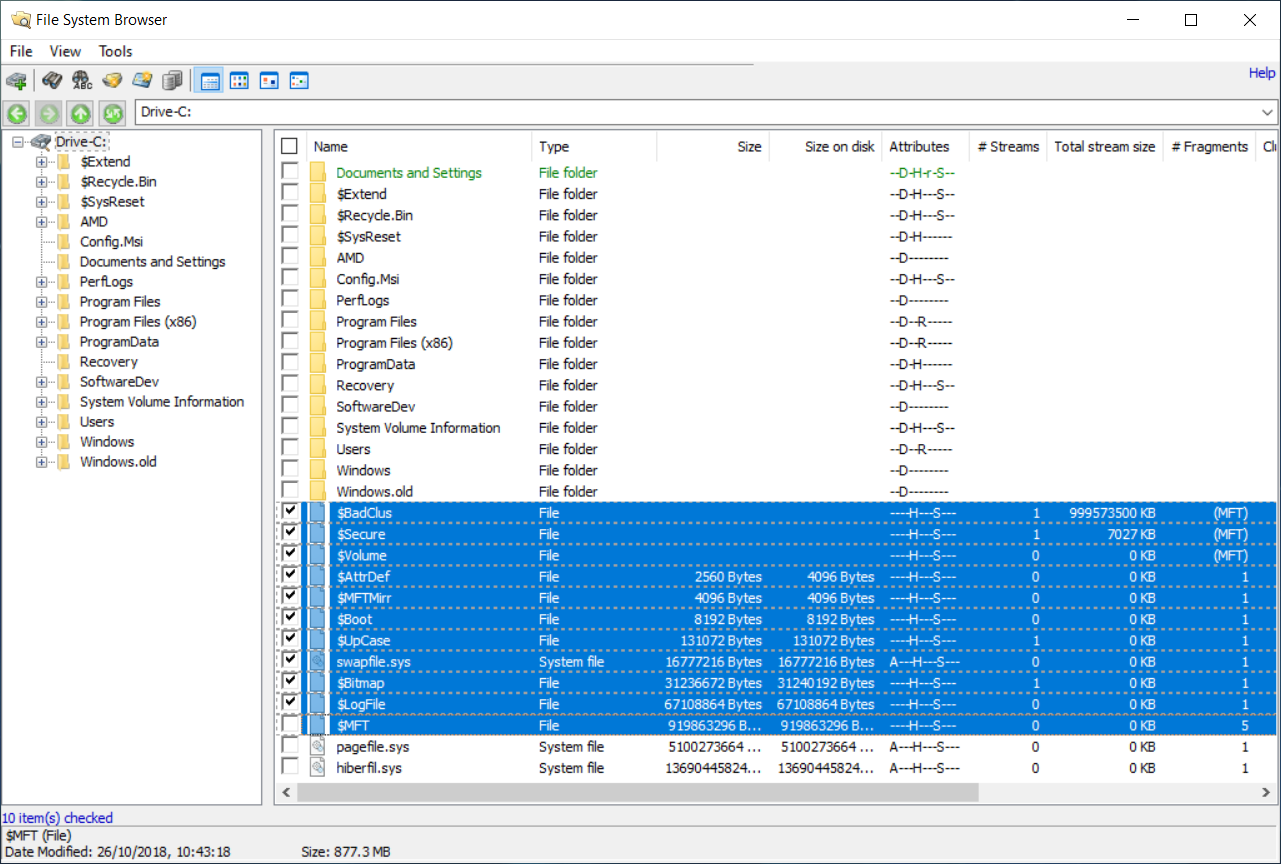
As can been seen above, OSF can display the hidden NTFS system files. Also known as Metafiles. The common files are $MFT - Master File Table. Contains details of all files on the volume. Each file on the disk has a corresponding record in the MFT with the file names, timestamps, attributes and location on the disk. Typically 12% if a volume's space is allocated for the MFT to grow into. OSF parses this file for you when you use the file system browser. $LogFile - A log of chances to the metafiles (Journaling) $Volume - Contains the volume's name, file system version and other status flags. $AttrDef - MFT attributes that associates numeric identifiers with names $Bitmap - A large array of bits indicating which clusters on the disk are free and which are used. $Boot - The volume boot record. Should always be the first cluster on the volume. $BadClus - A list of clusters that have been determined to be bad.
Other hidden and locked files can also be viewed using this method. Including many files that are hidden by rootkits and files inaccessible due to NTFS permissions.
If you wish to view the dates associated with NTFS files, from the Menu, Select tools > Options > and check the box ‘Show $File_Name dates (NTFS).
Note: OSForensics version 1.1 or higher required




