Scanning Standalone Registry Files for User Activity
By default, OSForensics will search for known Windows folders when scanning for registry data. If you have a set of registry files extracted from a system, you can scan them with the powerful User Activity module in OSForensics by placing them in the root directory of a disk that does not have Windows installed on it, such as a USB thumb drive for instance. You can then simply select this drive in OSForensics as the target of the User Activity scan and it will search the root directory for the registry files and parse the relevant artifacts.
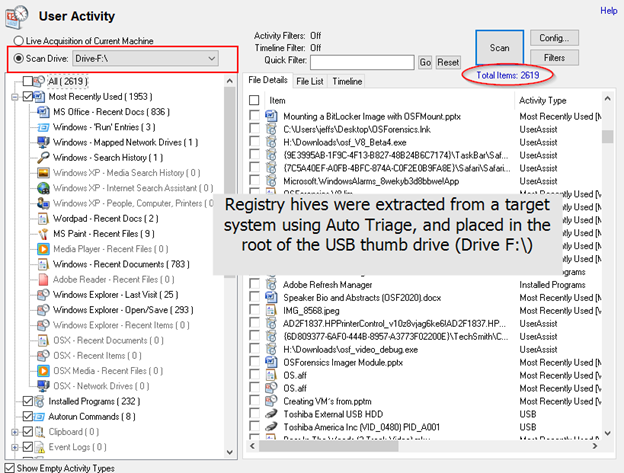
In the example above, over 2,600 artifacts were extracted from the SAM, SYSTEM, SOFTWARE, SECURITY and NTUSER.DAT registry hives within a few seconds using this method. This is an extremely quick and simple way to parse the most relevant data from a set of registry hives.




